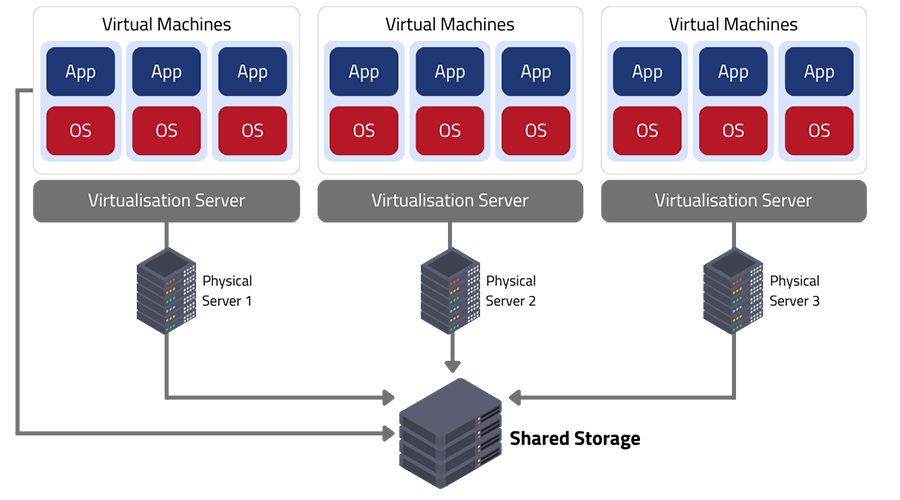
In the rapidly evolving business communication landscape, staying ahead of the curve is crucial. As organisations increasingly shift to remote and hybrid work models, the need for a seamless, efficient, and cost-effective communication system becomes paramount. Enter Microsoft Teams Direct Routing, a solution that not only streamlines communication but also significantly reduces costs, boosts productivity, and simplifies the overall communication infrastructure.
Table of contents
- The Rise of Microsoft Teams for PSTN Voice
- Cost Reduction: Streamline Your Communication Expenses
- Increasing Productivity: Unify Your Communication Tools
- Reducing Complexity: Simplify Your Communication Infrastructure
- Real-World Impact: The Shift to Teams for PSTN Voice
- Embrace the Future of Communication with Saicom
The Rise of Microsoft Teams for PSTN Voice
Microsoft Teams has seen explosive growth, becoming a central hub for collaboration in many organisations. According to recent statistics, over 270 million monthly active users are leveraging Teams for their communication and collaboration needs. A significant portion of this user base is also transitioning their Public Switched Telephone Network (PSTN) voice services to Teams, recognising the immense benefits it offers.
A study conducted by Forrester Consulting for Microsoft highlights several key benefits of integrating Teams for voice services:
- 291% Return on Investment (ROI): Companies reported a substantial ROI from using Microsoft Teams, reflecting significant cost savings and efficiency gains.
- <6 months Payback Period: Organisations saw a payback period of less than six months after going live with Microsoft Teams.
- $33.9M Benefits Present Value: The efficiencies from communicating and collaborating within Teams resulted in a present value benefit of $33.9 million.
- $8M Three-Year Benefit: Improved and integrated communication with Teams Phone delivered an $8 million benefit over three years.
Cost Reduction: Streamline Your Communication Expenses
One of the most compelling reasons to consider Microsoft Teams Direct Routing is the potential for cost savings. Traditional telephony systems come with high costs associated with hardware, maintenance, and separate service providers. With Direct Routing, these costs are significantly reduced. Here’s how:
- Elimination of On-Premise Hardware: By moving to a cloud-based system, businesses can avoid the hefty capital expenditure on PBX hardware and its ongoing maintenance costs.
- Lower Call Charges: Direct Routing allows companies to choose their own telecom providers, often leading to more competitive call rates.
- Consolidated Billing: Integrating PSTN services with Teams streamlines billing, reducing administrative overhead and simplifying budget management.
Increasing Productivity: Unify Your Communication Tools
Productivity is at the heart of any successful business. Microsoft Teams Direct Routing enhances productivity by integrating voice services into a single, unified platform. Here’s why this matters:
- Seamless Integration: With Direct Routing, employees can make and receive calls directly within Teams, without the need to switch between different applications. This integration leads to more efficient workflows and reduces the time spent on managing multiple communication tools.
- Enhanced Collaboration: Teams Direct Routing supports a range of features such as call transfer, call queues, and auto attendants, all of which enhance collaboration and ensure that the right calls reach the right people.
- Remote Work Enablement: As remote work becomes more prevalent, having a reliable, integrated communication system that works from anywhere is essential. Teams Direct Routing ensures that your employees stay connected and productive, no matter where they are.
Reducing Complexity: Simplify Your Communication Infrastructure
Managing a complex communication infrastructure can be a daunting task. Microsoft Teams Direct Routing simplifies this by consolidating all communication channels into a single platform. Here’s how it reduces complexity:
- Unified Management: With Direct Routing, IT teams can manage all communication services through the Teams admin center, reducing the complexity of managing multiple systems and vendors.
- Scalability: As your business grows, scaling your communication infrastructure is seamless with Direct Routing. There’s no need for additional hardware; simply add new users within the Teams platform.
- Reliability and Support: Leveraging Microsoft’s robust cloud infrastructure, which is backed by Microsoft’s extensive support network, ensures high availability and reliability.
Real-World Impact: The Shift to Teams for PSTN Voice
The trend of moving PSTN voice to Microsoft Teams is gaining momentum. Gartner predicts that by 2025, over 80% of enterprise voice services will be cloud-based, with a significant portion utilising Microsoft Teams Direct Routing. A 2023 survey by Nemertes Research found that 63% of organisations have either implemented or are planning to implement Microsoft Teams Direct Routing to replace their traditional PBX systems. Additionally, Microsoft reported a 50% year-over-year increase in the number of organisations using Teams as their primary telephony solution.
Furthermore, Forrester’s study underscores the tangible benefits organisations are experiencing:
- Office/Knowledge Worker Efficiencies: Increased collaboration within Microsoft Teams is estimated to save organisations $19.6 million over three years by reducing email traffic and time spent in formal meetings.
- Frontline Worker Efficiencies: Communication and collaboration improvements for frontline workers are projected to save $14.3 million over three years.
- Administrative Efficiencies: Streamlining and automating workflows within Teams contribute an estimated $8.1 million in savings.
- Announcements Platform Efficiencies: Using Teams for time-sensitive communications and training can save organisations over $3.3 million.
- Legacy Solution Retirement: Cost savings from retiring redundant collaboration platforms and equipment are estimated at $1.1 million.
- Reduced Service Tickets: Implementing chatbots in Teams to handle common queries can save an additional $645,000.
Embrace the Future of Communication with Saicom
At Saicom, we specialise in helping businesses harness the power of Microsoft Teams Direct Routing. Our tailored solutions ensure a smooth transition, optimised for cost savings, productivity gains, and simplified management.
By partnering with us, you can unlock the full potential of Microsoft Teams, transforming your communication infrastructure into a strategic asset that drives business success. Ready to reduce costs, increase productivity, and simplify your communication? Explore our Microsoft Teams Direct Routing solution here and take the first step towards a more efficient future.
Incorporating Microsoft Teams Direct Routing into your organisation is more than just an upgrade—it’s a strategic move towards a more streamlined, cost-effective, and productive communication environment. Join the growing number of businesses making the switch and experience the transformative benefits for yourself.
Greg de Chasteauneuf, Chief Technology Officer at Saicom