Cyber attackers are increasingly sophisticated, and they often lurk on networks for extended periods before they actually exfiltrate any data. This stealthy approach allows them to move laterally across the network, escalating privileges and searching for valuable assets. To combat this, organisations must deploy defensive measures that can detect and prevent lateral movement. One such measure is the use of honeypots, a form of deception technology that improves breach detection and mitigation.
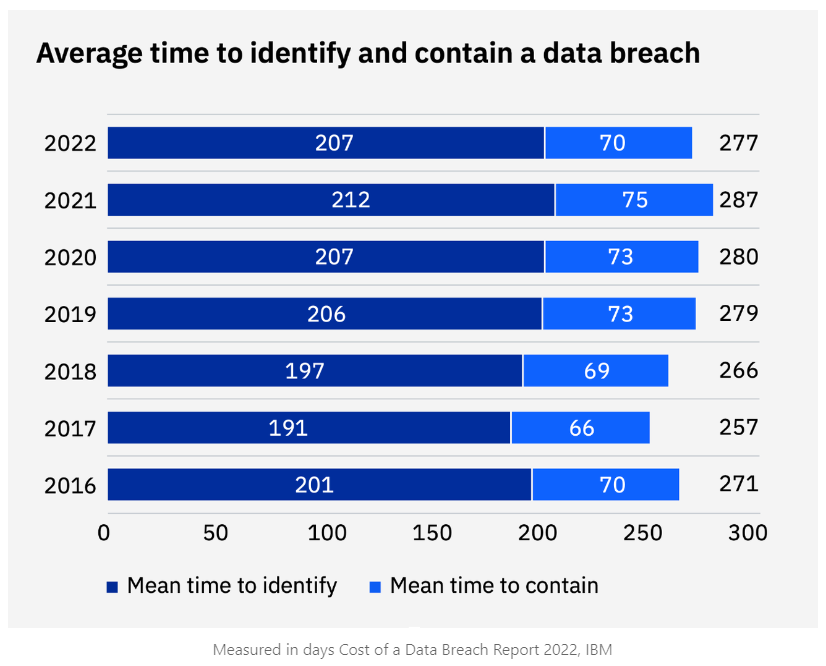
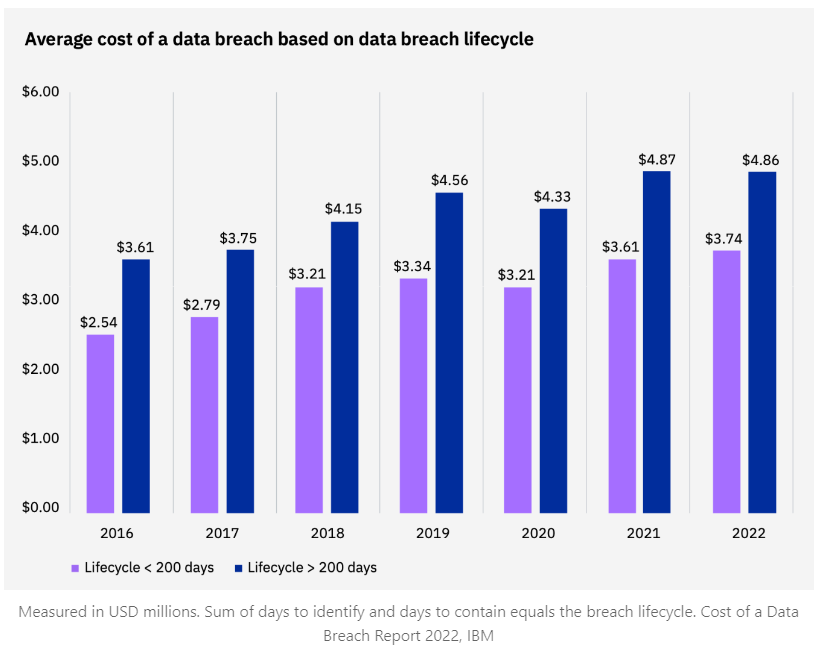
The rise in cyber crime has been striking, with global cyber crime costs projected to reach a staggering $10.5 trillion by 2025, a significant increase from $3 trillion in 2015, as reported by Cybersecurity Ventures. A 2022 study conducted by IBM and the Ponemon Institute found that it takes an average of 277 days to detect and contain a data breach, providing ample opportunity for attackers to inflict considerable damage. The financial impact of a breach tends to escalate the longer it remains undetected. According to the same study, the average cost of a data breach in South Africa increased from $3.21 million in 2021 to an estimated $3.63 million in 2022.
Honeypots are decoy systems or services, designed to appear as legitimate network assets. These decoys attract cyber attackers, luring them away from the actual valuable assets on the network. Honeypots are specifically configured to be vulnerable and enticing, mimicking the appearance and functionality of real systems.
When an attacker interacts with a honeypot, they inadvertently trigger an alert to the security team. This enables organisations to quickly detect and respond to a breach, thereby limiting the potential damage. Organisations can deploy these devices throughout their network that are configured to look like valuable content. Once probed, an alert is immediately sent, allowing the security team to intercept, investigate, and mitigate the breach.
For example, consider a financial institution that has deployed honeypots disguised as sensitive databases containing customer information. An attacker who gains access to the network may attempt to infiltrate these honeypots, believing them to be genuine targets. Upon interacting with the decoy, the attacker unknowingly triggers an alert, which is sent to the security team. This early warning allows the organisation to identify the breach, monitor the attacker’s actions, and ultimately mitigate the threat before any real damage is done to their systems or customer data.
Despite their effectiveness, honeypots are often seen as a grudge purchase, much like insurance. Many organisations only consider investing in honeypots after suffering a breach, when it is already too late. This mindset can leave businesses exposed to significant risks, especially considering the length of time attackers often spend on networks before being detected.
However, implementing honeypots within a network can be a simple and low-noise process. Modern honeypots can be quickly deployed with minimal configuration, allowing organisations to begin reaping the benefits without causing significant disruption to their existing network infrastructure.
Honeypots play a critical role in mitigating lateral movement in networks. They offer an effective method of detecting and responding to breaches, giving security teams the upper hand against cyber attackers. Although they may be seen as a grudge purchase, their ability to protect valuable assets and limit the damage caused by breaches makes them an essential component of a robust cybersecurity strategy.
Greg de Chasteauneuf, Chief Technology Officer at Saicom